what is needed to define interesting traffic in the creation of an ipsec tunnel?
CCNA Security v2.0 Chapter viii Answers – Implementing Network Security
CCNA Security Affiliate 8 Exam Answers
- Which transform gear up provides the best protection?
- crypto ipsec transform-set ESP-DES-SHA esp-aes-256 esp-sha-hmac*
- crypto ipsec transform-set ESP-DES-SHA esp-3des esp-sha-hmac
- crypto ipsec transform-fix ESP-DES-SHA esp-des esp-sha-hmac
- crypto ipsec transform-set ESP-DES-SHA esp-aes esp-des esp-sha-hmac
DES uses 56-scrap keys. 3DES uses 56-bit keys, but encrypts three times. AES uses 128-bit keys. AES-256 uses 256-bit keys and is the strongest.
- Which three ports must be open to verify that an IPsec VPN tunnel is operating properly? (Choose three.)
- 168
- 50*
- 169
- 501
- 500*
- 51*
- Refer to the exhibit. How will traffic that does not friction match that defined by access list 101 be treated by the router?
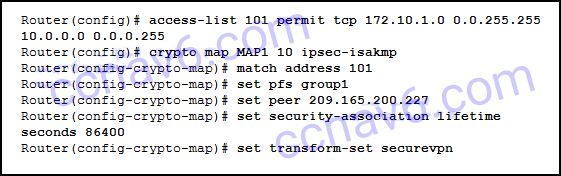
- It volition be sent unencrypted.*
- Information technology volition be sent encrypted.
- It will be blocked.
- It volition exist discarded.
The access list 101 is part of the crypto map configuration on the router. The purpose of the admission listing is to identify interesting traffic that should be sent encrypted over a VPN. Traffic that does not match the access-list is not interesting and is not sent encrypted just rather sent unencrypted in obviously text.
- What three protocols must be permitted through the company firewall for establishment of IPsec site-to-site VPNs? (Cull three.)
- HTTPS
- SSH
- AH*
- ISAKMP*
- NTP
- ESP*
ESP, AH, and ISAKMP must all be permitted through the perimeter routers and firewalls in lodge for IPsec site-to-site VPNs to be established. NTP and HTTPS are application protocols and are not required for IPsec.
- When is a security association (SA) created if an IPsec VPN tunnel is used to connect between two sites?
- subsequently the tunnel is created, but earlier traffic is sent
- only during Phase 2
- but during Stage 1
- during both Phase 1 and 2*
As seen in the 8.4.1.one Figure, an IPsec VPN connectedness creates two SAs: (one) at the completion of the IKE Phase 1 once the peers negotiate the IKE SA policy, and (2) at the stop of IKE Stage 2 after the transform sets are negotiated.
- In which situation would the Cisco Discovery Protocol exist disabled?
- when a Cisco VoIP phone attaches to a Cisco switch
- when a Cisco switch connects to some other Cisco switch
- when a Cisco switch connects to a Cisco router
- when a PC with Cisco IP Communicator installed connects to a Cisco switch*
Cisco Discovery Protocol should exist disabled on ports that practice non connect to other Cisco devices. Even though the PC has a Cisco software production installed, the port to which the PC connects should take Cisco Discovery Protocol disabled because of the network data that can be derived from capturing Cisco Discovery Protocol letters.
- Which 2 statements accurately describe characteristics of IPsec? (Choose ii.)
- IPsec works at the send layer and protects data at the network layer.
- IPsec is a framework of proprietary standards that depend on Cisco specific algorithms.
- IPsec is a framework of standards developed by Cisco that relies on OSI algorithms.
- IPsec is a framework of open up standards that relies on existing algorithms.*
- IPsec works at the network layer and operates over all Layer 2 protocols.*
- IPsec works at the application layer and protects all application data.
IPsec can secure a path between two network devices. IPsec tin provide the following security functions:
Confidentiality – IPsec ensures confidentiality by using encryption.
Integrity – IPsec ensures that data arrives unchanged at the destination using a hash algorithm, such as MD5 or SHA.
Authentication – IPsec uses Cyberspace Fundamental Exchange (IKE) to authenticate users and devices that can acquit out communication independently. IKE uses several types of hallmark, including username and password, one-time countersign, biometrics, pre-shared keys (PSKs), and digital certificates.
Secure cardinal exchange – IPsec uses the Diffie-Hellman (DH) algorithm to provide a public key exchange method for two peers to establish a shared undercover key. - Which action do IPsec peers take during the IKE Phase 2 exchange?
- exchange of DH keys
- negotiation of IPsec policy*
- negotiation of IKE policy sets
- verification of peer identity
The IKE protocol executes in two phases. During Phase 1 the two sides negotiate IKE policy sets, cosign each other, and set up a secure channel. During the second phase IKE negotiates security associations between the peers.
- Which statement describes the effect of central length in deterring an attacker from hacking through an encryption key?
- The length of a key does non affect the caste of security.
- The shorter the central, the harder it is to pause.
- The length of a key volition not vary between encryption algorithms.
- The longer the key, the more key possibilities be.*
While preventing brute-forcefulness attacks and other forced decryption concerns, the longer the key length, the harder information technology is to intermission. A 64-bit key tin can take one year to break with a sophisticated reckoner, while a 128-bit key may take 1019 years to decrypt. Unlike encryption algorithms will provide varying key lengths for implementation.
- What is the purpose of configuring multiple crypto ACLs when building a VPN connexion between remote sites?
- By applying the ACL on a public interface, multiple crypto ACLs tin be congenital to forbid public users from connecting to the VPN-enabled router.
- Multiple crypto ACLs can ascertain multiple remote peers for connecting with a VPN-enabled router beyond the Internet or network.
- Multiple crypto ACLs can be configured to deny specific network traffic from crossing a VPN.
- When multiple combinations of IPsec protection are beingness chosen, multiple crypto ACLs tin ascertain different traffic types.*
A crypto ACL can define "interesting traffic" that is used to build a VPN, and forward that "interesting traffic" beyond the VPN to some other VPN-enabled router. Multiple crypto ACLs are used to define multiple dissimilar types of traffic and apply different IPsec protection corresponding to the dissimilar types of traffic.
- Consider the post-obit configuration on a Cisco ASA:
crypto ipsec transform-fix ESP-DES-SHA esp-des esp-sha-hmac
What is the purpose of this control?- to ascertain the ISAKMP parameters that are used to establish the tunnel
- to define the encryption and integrity algorithms that are used to build the IPsec tunnel*
- to define what traffic is immune through and protected past the tunnel
- to define only the allowed encryption algorithms
The transform set is negotiated during Stage 2 of the IPsec VPN connection process. The purpose of the transform set is to ascertain what encryption and authentication schemes can be used. The device doing the VPN initiation offers the acceptable transform sets in social club of preference, in this case, ESP authentication using DES for encryption or ESP authentication using SHA-HMAC authentication and integrity for the data payload. Think that ESP provides confidentiality with encryption and integrity with authentication. The ESP-DES-SHA is the name of the transform set. The parameters that follow (esp-des and esp-sha-hmac) are the specific types of encryption or authentication that is supported by the ASA for the VPN tunnel that uses this transform ready.
- Which technique is necessary to ensure a private transfer of information using a VPN?
- encryption*
- authorisation
- virtualization
- scalability
Confidential and secure transfers of information with VPNs require data encryption.
- Which statement describes a VPN?
- VPNs utilize open source virtualization software to create the tunnel through the Internet.
- VPNs utilize virtual connections to create a private network through a public network.*
- VPNs utilise dedicated concrete connections to transfer data betwixt remote users.
- VPNs use logical connections to create public networks through the Internet.
- Which protocol provides authentication, integrity, and confidentiality services and is a type of VPN?
- ESP
- IPsec*
- MD5
- AES
IPsec services allow for hallmark, integrity, access control, and confidentiality. With IPsec, the data exchanged between remote sites can be encrypted and verified. Both remote-access and site-to-site VPNs tin can be deployed using IPsec.
- Which 3 statements describe the IPsec protocol framework? (Choose iii.)
- AH provides integrity and hallmark.*
- ESP provides encryption, authentication, and integrity.*
- AH uses IP protocol 51.*
- AH provides encryption and integrity.
- ESP uses UDP protocol 50.
- ESP requires both authentication and encryption.
The two chief protocols used with IPsec are AH and ESP. AH is protocol number 51 and provides data authentication and integrity for IP packets that are exchanged between the peers. ESP, which is protocol number l, performs packet encryption.
- Which argument accurately describes a characteristic of IPsec?
- IPsec works at the application layer and protects all application data.
- IPsec is a framework of standards developed by Cisco that relies on OSI algorithms.
- IPsec is a framework of proprietary standards that depend on Cisco specific algorithms.
- IPsec works at the transport layer and protects data at the network layer.
- IPsec is a framework of open standards that relies on existing algorithms.*
IPsec can secure a path between two network devices. IPsec tin provide the following security functions:
Confidentiality – IPsec ensures confidentiality by using encryption.
Integrity – IPsec ensures that information arrives unchanged at the destination using a hash algorithm, such equally MD5 or SHA.
Authentication – IPsec uses Internet Key Exchange (IKE) to cosign users and devices that tin carry out advice independently. IKE uses several types of authentication, including username and password, 1-fourth dimension password, biometrics, pre-shared keys (PSKs), and digital certificates.
Secure key commutation- IPsec uses the Diffie-Hellman (DH) algorithm to provide a public key exchange method for ii peers to establish a shared undercover primal. - Which two IPsec protocols are used to provide data integrity?
- SHA*
- AES
- DH
- MD5*
- RSA
The IPsec framework uses diverse protocols and algorithms to provide data confidentiality, data integrity, authentication, and secure cardinal exchange. Ii popular algorithms used to ensure that data is non intercepted and modified (data integrity) are MD5 and SHA. AES is an encryption protocol and provides data confidentiality. DH (Diffie-Hellman) is an algorithm used for fundamental exchange. RSA is an algorithm used for hallmark.
- What is the office of the Diffie-Hellman algorithm within the IPsec framework?
- provides authentication
- allows peers to substitution shared keys*
- guarantees message integrity
- provides stiff information encryption
The IPsec framework uses diverse protocols and algorithms to provide information confidentiality, information integrity, authentication, and secure key exchange. DH (Diffie-Hellman) is an algorithm used for key exchange. DH is a public central commutation method that allows two IPsec peers to establish a shared secret key over an insecure channel.
- Refer to the exhibit. What HMAC algorithm is existence used to provide data integrity?
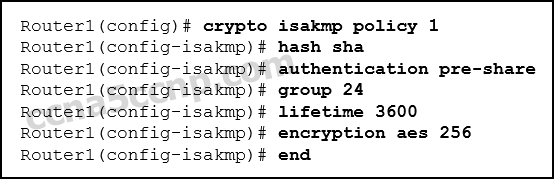
- MD5
- AES
- SHA*
- DH
Two pop algorithms that are used to ensure that data is not intercepted and modified (data integrity) are MD5 and SHA. The command Router1(config-isakmp)# hash sha indicates that SHA is existence used. AES is an encryption protocol and provides data confidentiality. DH (Diffie-Hellman) is an algorithm that is used for central commutation. RSA is an algorithm used for hallmark.
- What is needed to define interesting traffic in the creation of an IPsec tunnel?
- security associations
- hashing algorithm
- admission list*
- transform set
In order to bring upward an IPsec tunnel, an access list must be configured with a allow statement that will identify interesting traffic. Once interesting traffic is detected past matching the access list, the tunnel security associations can be negotiated.
- Refer to the exhibit. What algorithm will be used for providing confidentiality?
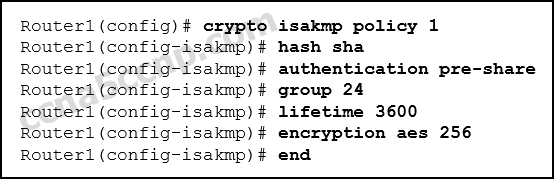
- RSA
- Diffie-Hellman
- DES
- AES*
The IPsec framework uses diverse protocols and algorithms to provide information confidentiality, data integrity, authentication, and secure key exchange. Ii popular algorithms that are used to ensure that data is non intercepted and modified (data integrity) are MD5 and SHA. AES is an encryption protocol and provides information confidentiality. DH (Diffie-Hellman) is an algorithm that is used for key exchange. RSA is an algorithm used for authentication.
- Which two protocols must be allowed for an IPsec VPN tunnel is operate properly? (Choose two.)
- 501
- 500
- 51*
- 168
- 50*
- 169
ESP uses protocol 50. AH uses protocol 51. ISAKMP uses UDP port 500.
- What is the purpose of NAT-T?
- enables NAT for PC-based VPN clients
- permits VPN to piece of work when NAT is being used on i or both ends of the VPN*
- upgrades NAT for IPv4
- allows NAT to be used for IPv6 addresses
Establishing a VPN betwixt ii sites has been a challenge when NAT is involved at either cease of the tunnel. The enhanced version of original IKE, IKE version 2, now supports NAT-T. NAT-T has the ability to encapsulate ESP packets inside UDP and then that the VPN tunnel tin be established through a device that has NAT enabled.
- Which term describes a situation where VPN traffic that is is received by an interface is routed back out that same interface?
- GRE
- split tunneling
- MPLS
- hairpinning*
Hairpinning allows VPN traffic that is received on a single interface to be routed dorsum out that same interface. Split tunneling allows traffic that originates from a remote-admission client to be split according to traffic that must cross a VPN and traffic destined for the public Net. MPLS and GRE are ii types of Layer 3 VPNs.
- What is an important characteristic of remote-access VPNs?
- The VPN configuration is identical between the remote devices.
- Internal hosts have no cognition of the VPN.
- Information required to establish the VPN must remain static.
- The VPN connection is initiated past the remote user.*
With remote-access VPNs, the remote user does not necessarily accept the VPN connection set upward at all times. The remote user PC is responsible for initiating the VPN. Information required to establish the VPN connexion changes dynamically depending on the location of the user when attempting to connect.
- Which type of site-to-site VPN uses trusted group members to eliminate point-to-point IPsec tunnels betwixt the members of a group?
- DMVPN
- GRE
- GETVPN*
- MPLS
Group Encrypted Transport VPN (GETVPN) uses a trusted grouping to eliminate point-to-point tunnels and their associated overlay routing. GETVPN is frequently described as "tunnel-less." Dynamic Multipoint VPN (DMVPN) enables auto-provisioning of site-to-site IPsec VPNs using a combination of three Cisco IOS features: NHRP, GRE, and IPsec VPNs. Generic Routing Encapsulation (GRE) is a tunneling protocol developed past Cisco that encapsulates multiprotocol traffic between remote Cisco routers, but does not encrypt data. An MPLS VPN consists of a ready of sites that are interconnected by means of an MPLS provider core network.
- Refer to the exhibit. Which pair of crypto isakmp key commands would correctly configure PSK on the 2 routers?
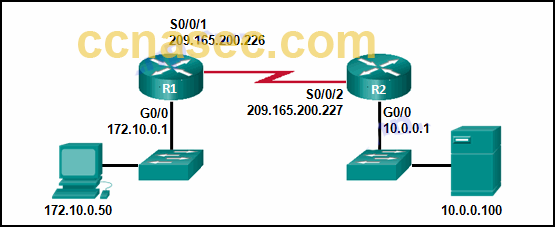
- R1(config)# crypto isakmp key cisco123 accost 209.165.200.227
R2(config)# crypto isakmp primal cisco123 accost 209.165.200.226* - R1(config)# crypto isakmp key cisco123 address 209.165.200.226
R2(config)# crypto isakmp key cisco123 address 209.165.200.227 - R1(config)# crypto isakmp key cisco123 hostname R1
R2(config)# crypto isakmp cardinal cisco123 hostname R2 - R1(config)# crypto isakmp key cisco123 address 209.165.200.226
R2(config)# crypto isakmp key secure address 209.165.200.227
The correct syntax of the crypto isakmp key control is equally follows:
crypto isakmp fundamental keystring address peer-address
or
crypto isakmp keykeystring hostname peer-hostnameSo, the right answer would be the following:
R1(config)# crypto isakmp key cisco123 address 209.165.200.227
R2(config)# crypto isakmp key cisco123 address 209.165.200.226 - R1(config)# crypto isakmp key cisco123 accost 209.165.200.227
Source: https://ccnasec.com/ccna-security-v2-0-chapter-8-answers-implementing-network-security.html#:~:text=In%20order%20to%20bring%20up,Refer%20to%20the%20exhibit.
0 Response to "what is needed to define interesting traffic in the creation of an ipsec tunnel?"
ارسال یک نظر